Denial-of-service DoS and distributed denial-of-service DDoS attacks. If your web application or other system is hacked and used to launch an attack on another victim forensic investigation may lead law enforcement to your systems.

Smart Budget Grocery Shopping Infographic Budgeting Shopping Infographic Budget Grocery Shopping
In cryptography variable-length plaintext messages often have to be padded to be compatible with the underlying cryptographic primitive.

Failing to prevent an attack all but invites an attack. To poison an AI system the attacker must compromise the learning process in a way such that the model fails on certain attacker-chosen inputs or learns a backdoor that the attacker can use to control the model in the future. Its a tough job to secure a distributed system especially when they otherwise provide value to users and organizations through ease of use at scale. Many more journalists undergo harassment physical attacks jail and censorship.
In cryptography a padding oracle attack is an attack which uses the padding validation of a cryptographic message to decrypt the ciphertext. Usually if an attacker fails at their first attempt they may or may not progress and. If you dont like bananas try other high-potassium foods which include.
Unfortunately these threats are coming at a time when news media particularly newspapers are undergoing extreme disruption to their business. Keeping journalists safe can be an expensive proposition. A man-in-the-middle attack MITM attack is a cyber attack where an attacker relays and possibly alters communication between two parties who believe they are communicating directly.
One motivation is to poison a model so that it fails on a particular task or types of input. These attacks are known as DLL preloading attacks and are common to all operating systems that support dynamically loading shared DLL libraries. The attack relies on having a padding oracle who freely responds to queries about whether a message is correctly padded or not.
The earths computing would be much safer without the Internet too but the same way a villain might poison a. Even systems that dont provide C-box capabilities can be. These attacks inundate a systems resources overwhelming them and preventing responses to service requests and greatly reducing the systems ability to perform.
Try to detach yourself recognizing the attack as more about the attackers emotional needs and communication skills. Cybercriminals often try to cover their tracks by staging high-profile attacks from intermediate compromised systems. The sweet treat is packed with potassium and other heart-healthy nutrients.
The effect of such attacks could be that an attacker can execute code in the context of the user who. We will also assume that you have at least two computers that are on the same network. Try not take the attack personally.
We will assume you are using Windows for this exercise. Theres no single step to prevent all interception attacks on any network protocol other than removing the protocol completely. Firewalls can be used to stop simple DoS attacks by blocking all traffic coming from an attacker by identifying his IP.
The culture of impunity is intimidating many others into exile or silence. This allows an IDS to try to prevent further attacks from occurring after initial attacks are detected. For example if a military is training an AI system to detect enemy aircraft the enemy may try to poison the learned model so that it fails.
In that case the onus is on you to prove that you were not complicit in the attack your systems were secured according to the current state of the art and your staff followed all. However most commercially available ID systems are equipped with some form of countermeasure C-box capability ranging from shutting down TCP connections to modifying router filter lists. Very few of the cases have ever been resolved.
Next consider the following pseudocode. The attack is not a reflection on you. If an attacker gains control of one of the directories they can force the application to load a malicious copy of the DLL instead of the DLL that it was expecting.
Now in case its not immediately obvious if somevar sent by the user of course is set for example to. Routers can be configured via the Access Control List to limit access to the network and drop suspected illegal traffic. Many ID systems are designed only as alarms.
This allows the attacker to relay communication listen in and even modify what each party is saying. The goal of DoS or DDoS is usually service denial or setting up a different second attack. Hit and run attacks Another of the most common router attacks is something called a hit and run attack and they are designed as one off attack on a specific network or router.
Companies and governments must focus on detection and. Although we cant prevent cyberattacks we can prepare for them. Man-in-the-middle attacks enable eavesdropping between people.
Hot and run attacks are often referred to as test hacks and also occur when malicious data is injected into router through code. To help prevent attacks snack on bananas. May 10 2017.
A onclickalert documentcookie the resulting output is.

The Fastest And Slowest Internet In The World Slow Internet Internet Speed Infographic

Pin On Maine Engagement Photography
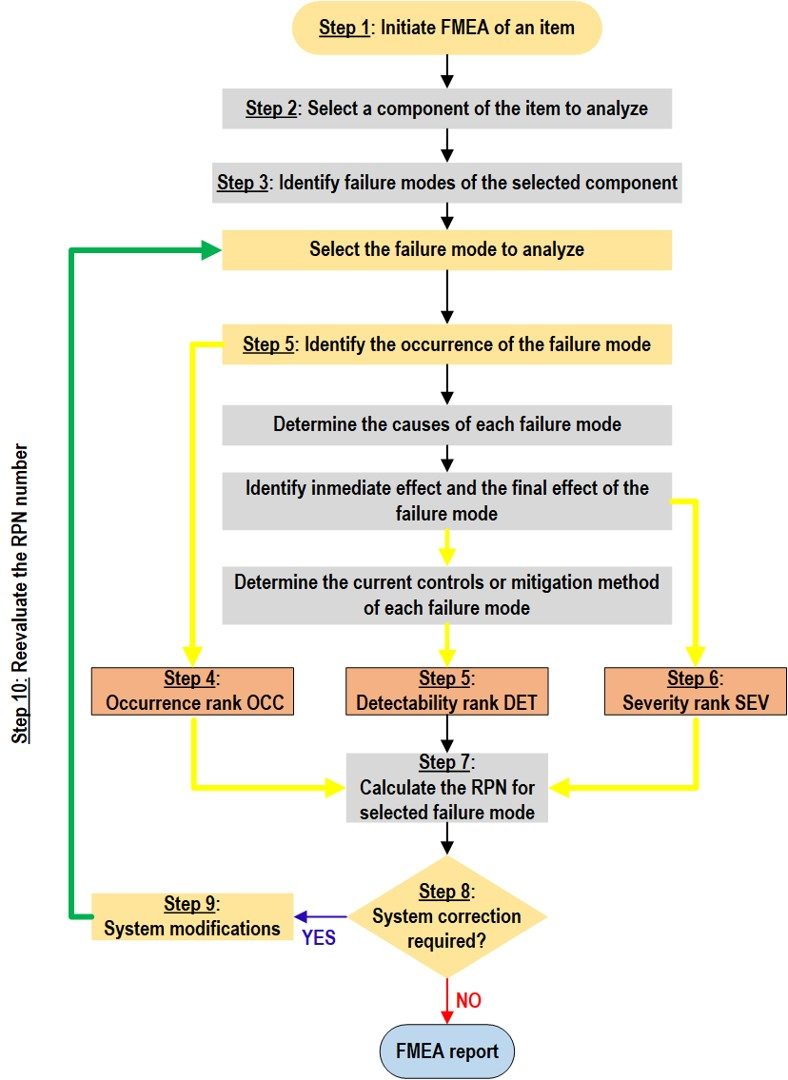
Energies Free Full Text Classical Failure Modes And Effects Analysis In The Context Of Smart Grid Cyber Physical Systems Html

Top 10 Daily Habits That Are Bad For Your Heart Avoid Them Keep Your Heart Healthy You May Be Physically Active Daily Habits Holistic Healing Habits

Pin On 100 Examples Online Form Templates

Co Q10 Or Coenzyme Q10 Is An Enzyme That Helps To Boost Cell Activity And Has Tremendous Benefits That Make It Very Popular Amon Cells Activity Coenzyme Health

Pin On Mandala Art Design Ideas

Pin On Health Tips For Everyone










